Archive
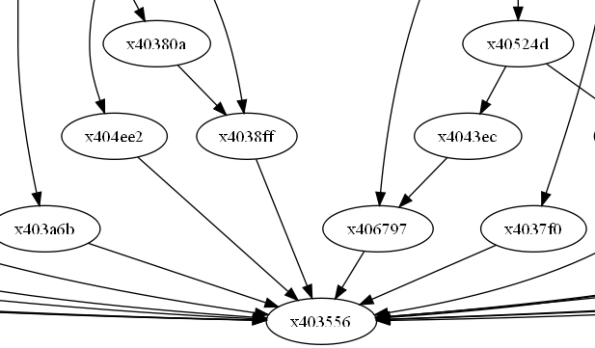
ROPC — Turing complete ROP compiler (part 3, implementation)
This is the third (and last) post in a series (first post here, second here) about ROPC, describing implementation of its features like tables, conditional jumps, recursive calls, etc. Please familiarize yourself with the two first posts, otherwise this one might be hard to follow.
ROPC — Turing complete ROP compiler (part 2, language)
This is the second post in a series (first post here) describing ROPC. Programs accepted by the compiler are written in ROPL (Return Oriented Programming Language). ROP programs are usually used as stage 0 payloads. They compute addresses, change memory protections, call few OS APIs. For this reason, language expressing them doesn’t have to be complex.
ROPC — Turing complete ROP compiler (part 1)
This is a long overdue post describing ROPC (Return Oriented Programming Compiler, available here: https://github.com/pakt/ropc) with its own “higher level” language and features like conditional jumps, loops, functions (even recursive ones), tables, etc.. ROPC was released in 2012. Since then, Christian Heitman made a fork [0] capable of compiling ROP programs expressed in C (!).
Generalized birthday paradox — keygenme3 by Dcoder
The birthday problem [0] asks what’s the probability that among people at least two of them have the same birthday. The “paradox” is that the answer is counterintuitive — in a group of 23, the probability is close to 50%.
DeCV — a decompiler for Code Virtualizer by Oreans
Code Virtualizer is a software protection solution using heavy obfuscation. Citing the author’s website [5]:
Code Virtualizer is a powerful code-obfuscation system that helps developers protect their sensitive code areas against Reverse Engineering while requiring minimum system resources.
Code Virtualizer can generate multiple types of virtual machines with a different instruction set for each one. This means that a specific block of Intel x86 instructions can be converted into different instruction set for each machine, preventing an attacker from recognizing any generated virtual opcode after the transformation from x86 instructions.
This post describes DeCV — a decompiler for Code Virtualizer.
Leaking information using timing attacks on hash tables, part 2
This is the second part of Leaking information using timing attacks on hash tables, discussing implementation details of the leak. Read the first part for a high level overview.
Leaking information with timing attacks on hashtables, part 1
Timing attacks [1] are an important subclass of side channel attacks used to reveal cryptographic secrets, basing only on time needed by targeted devices or applications to perform specific computations.
It turns out these attacks can be applied in a more prosaic context — instead of encryption keys, they can help us leak pointers to objects on the heap or, if we are lucky, in .code/.data sections of targeted application. Leaking a pointer with fixed RVA reveals the imagebase, so ASLR becomes ineffective (ROP). Leaking a heap pointer makes expoitation of WRITE-ANYWHERE bugs easier, so in both cases it’s a win :).
This post provides a high-level description of a POC implementation of a timing attack on hashtable used in Firefox (tested on v4, v13, v14). POC is quite fast (takes few secs) and leaks a heap pointer to a JS object. A detailed explanation will be provided in a different post (part 2).
Speed up your fuzzfarm: fast hit tracing
The fuzzing methodology introduced by Charlie Miller [1] was widely adopted in the security industry, as it is indeed an effective and low cost method of finding bugs.
The idea is:
- collect a lot of sample files
- let your target application parse them all
- collect the set of basic blocks executed for every file
- calculate the minimal set of samples that covers all of the collected basic blocks
- flip random bytes in files from that set and wait for a crash
It’s a simple process, but all implementations I heard of suffer from an interesting performance bottleneck in the basic block tracing part.
If your tracer takes >1min per file, you can speed it up to take only few seconds, with just a few simple observations.
Exploiting CVE-2011-2371 (FF reduceRight) without non-ASLR modules
CVE-2011-2371 (found by Chris Rohlf and Yan Ivnitskiy) is a bug in Firefox versions <= 4.0.1. It has an interesting property of being a code-exec and an info-leak bug at the same time. Unfortunately, all public exploits targeting this vulnerability rely on non-ASLR modules (like those present in Java).
In this post I’ll show how to exploit this vulnerability on Firefox 4.0.1/Window 7, by leaking imagebase of one of Firefox’s modules, thus circumventing ASLR without any additional dependencies.
Hyperelliptic curve crypto — Dcoder’s keygenme #2
Apparently ordinary elliptic curves in crackmes are getting boring, so Dcoder decided to make things interesting with hyperelliptic curves. Due to intricate nature of HE curves, performing computations on them is more expensive, than for ordinary curves, but on the other hand HE curves provide superior bitstrength security, with regard to size of the base field, they are defined over.
In this blog post, I will try to introduce HE curves, and how to use them in crypto. Using that knowledgle, it will be easy to analyze and break a signature scheme implemented in keygenme #2 by Dcoder. Note that this won’t be a rigorous mathematical dissertation, but a “tutorial” for mathematically inclined programmer :).